POC Checklist
Platform requirements
➢ Scalability to match traffic demands and provide continuous protection without loss of performance
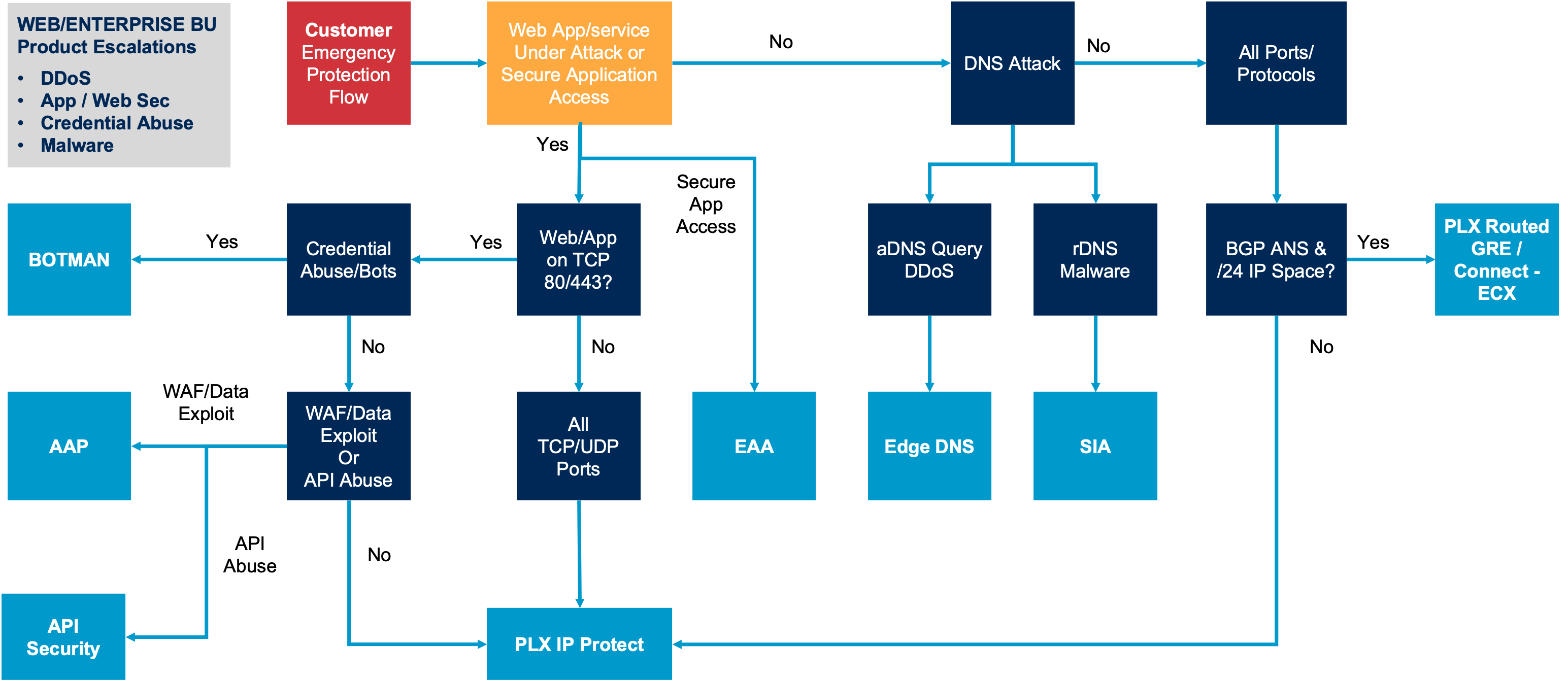
➢ Network layer [L3/4] distributed denial-of-service (DDoS) mitigation with a zero-second service-level agreement
➢ Architecture that can overcome the challenges of geographically dispersed applications
➢ Visibility into who is attacking, the frequency of attacks, and the severity of attacks with crowd-sourced attack intelligence across the platform
➢ Audit log capabilities to ensure proper usage
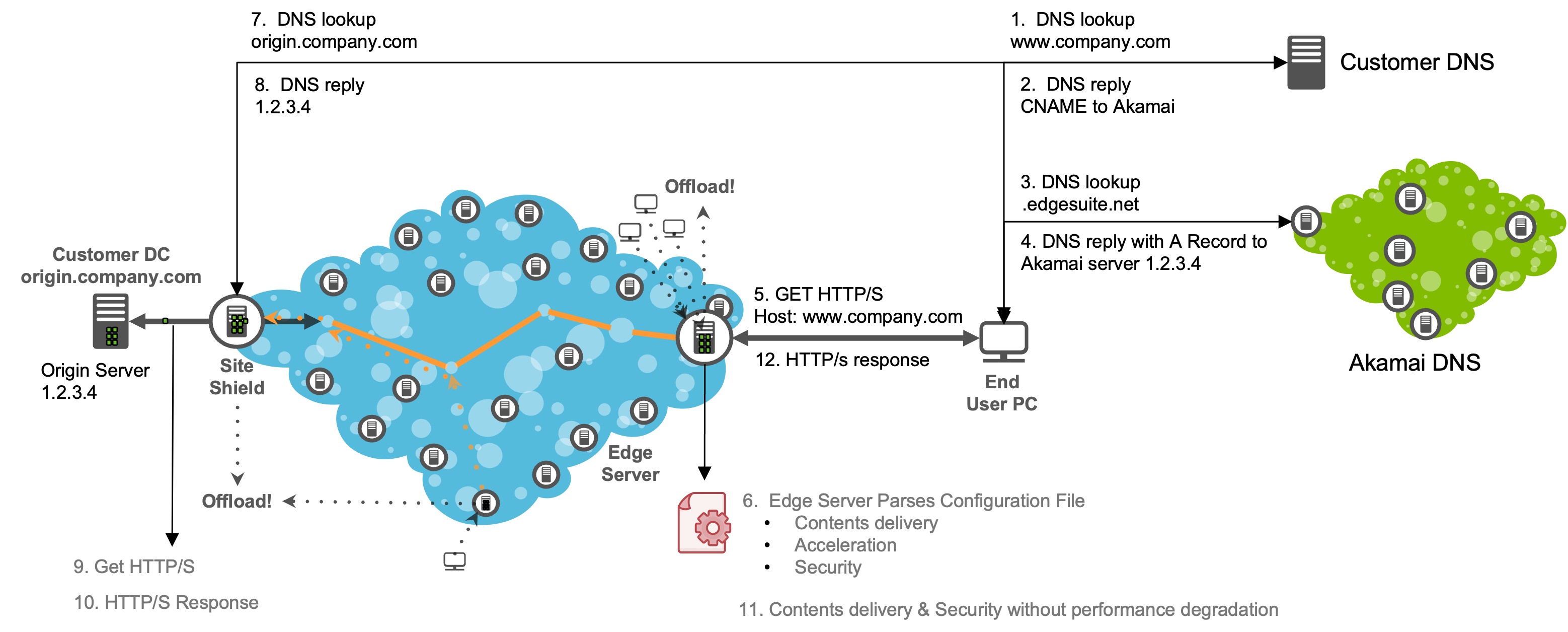
➢ Reverse proxy with web traffic via ports 80 and 443
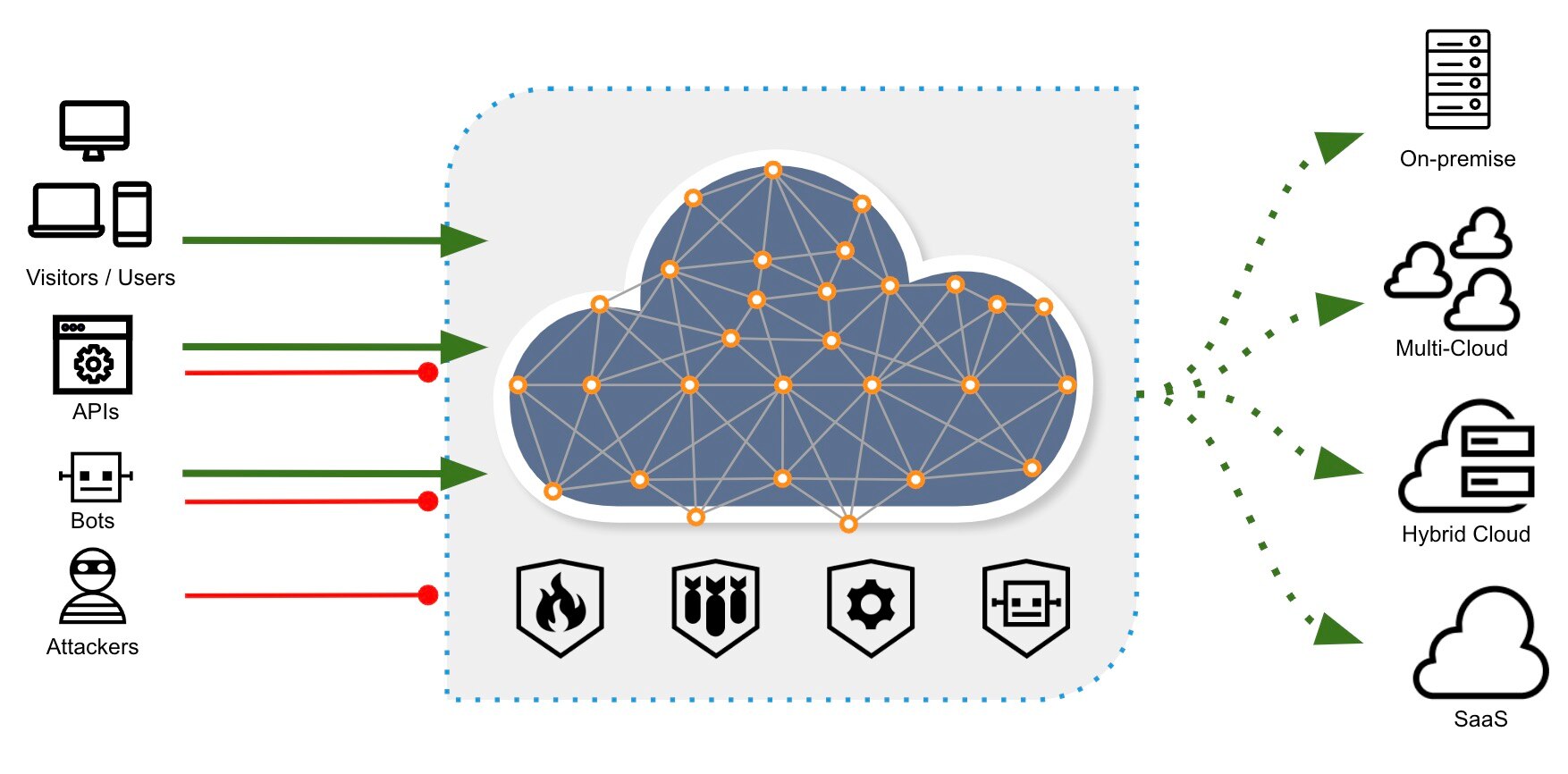
➢ Protection of on-premises, private, or public cloud (including multi-cloud or hybrid-cloud) site origins
➢ Network privacy protections with SSL/TLS encryption
Web Application Firewall and DDoS Protection
➢ Detection beyond signature-based attacks with anomaly and risk-based scoring
➢ Fully managed WAF rules to eliminate the need for continuous configuration and updates
➢ Machine learning, data mining, and heuristics-driven detection capabilities to identify rapidly evolving threats
➢ Client reputation scoring and intelligence for both individual and shared IP addresses
➢ Automatic web application firewall(WAF) rule updates with continuous real-time threat intelligence from security researchers
➢ Custom rules to quickly protect against specific traffic patterns (virtual patching)
➢ Ability to test new or updated WAF rules against live traffic before deploying to production
➢ Request rate limits to protect against automated or excessive bot traffic
➢ Protection (at a minimum) against SQL injection, XSS, file inclusion, command injection, SSRF, SSI, and XXE
➢ Protection from direct-to-origin
➢ Fully customizable predefined rules to meet specific customer requirements
➢ IP/Geography controls via multiple network lists to block or allow traffic from specific IP, subnet, or geographic areas
➢ Protection from application layer [L7] volumetric DoS attacks designed to overwhelm web servers with recursive application activity
➢ Protection from automated clients, such as vulnerability scanning and web attack tools
API Visibility, Protection and Control
➢ Automatic discovery and profiling of unknown and/or changing APIs (including API endpoints, characteristics, and definitions)
➢ Rate controls (throttling) for API endpoints based on API key
➢ Automatic inspection of XML and JSON requests to detect API-based attacks
➢ API network lists (allowlists/blocklists) based on IP/Geography
➢ Custom API inspection rules to meet specific user requirements
➢ API lifecycle management with versioning
➢ Ability to predefine acceptable XML and JSON object formats that restrict the size, type, and depth of API requests
➢ Secure authentication and authorization via JSON Web Token (JWT) validation
➢ Protection of API back-end infrastructures from low and slow attacks designed to exhaust resources (e.g., Slow Post, Slow Get)
➢ Definition of allowed API requests by key (quota for each key defined independently) for full control over consumption
➢ Real-time alerts, reporting, and dashboards at the API level
➢ API onboarding using standard API definitions (Swagger/OAS and RAML)
Flexible Management
➢ Open APIs and the CLI to integrate security configuration tasks into CI/CD processes
➢ Real-time dashboards, reporting, and heuristics-driven alerting capabilities
➢ Integration with on-premises and cloud-based security information and event management (SIEM) applications
➢ Centralized user interface (UI) to access detailed attack telemetry and analyze security events
➢ Full staging environment and the ability to implement change control
➢ Flexibility to manage WAAP via high-touch controls and/or fully automated protections
➢ Self-tuning security protections that automatically adapt to your traffic
➢ Fully managed security services to offload or augment your security management, monitoring, and threat mitigation