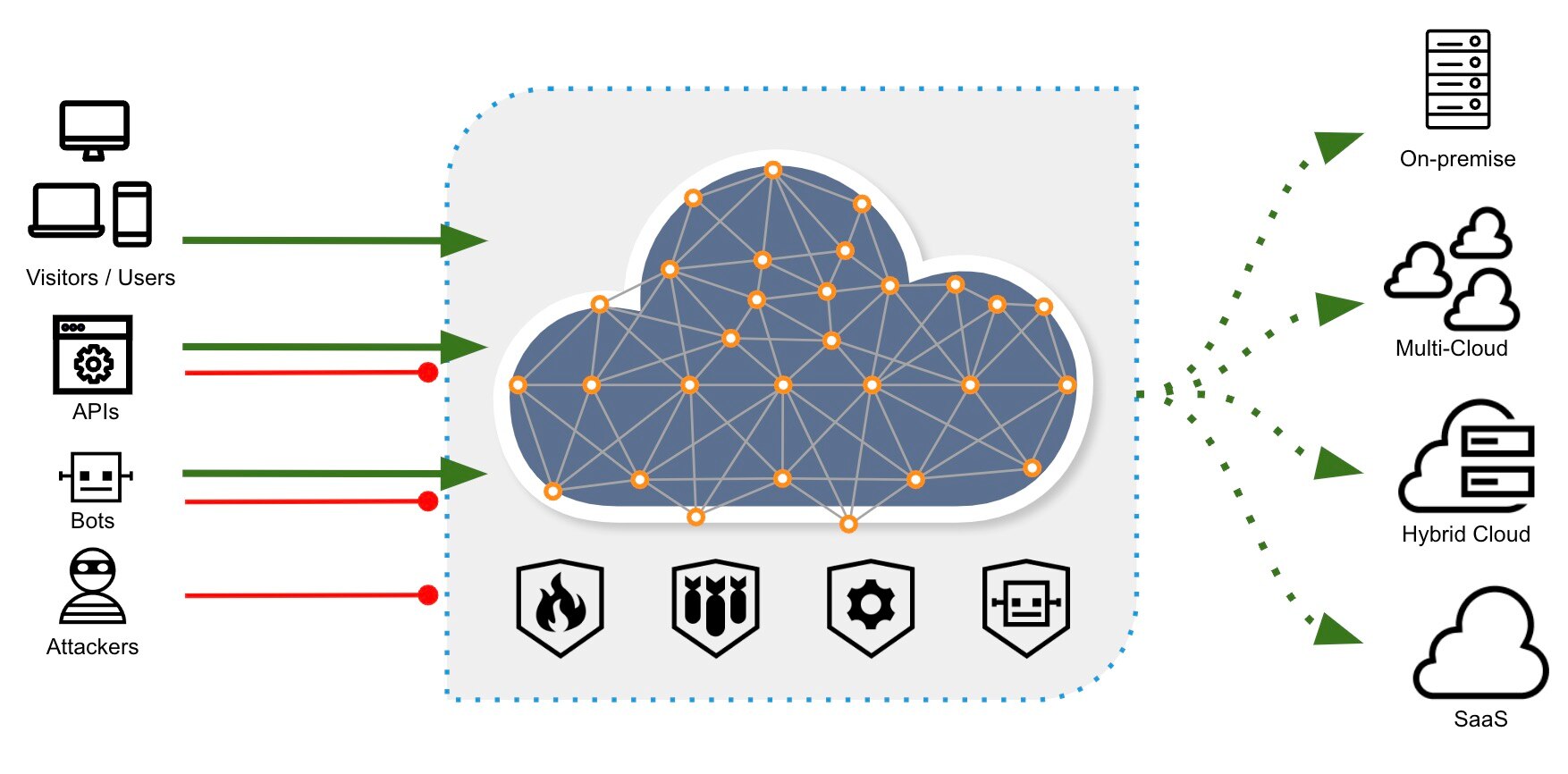
Apps and APIs - Protect your brand by securing apps and APIs from persistent threats

Applications run our world. But as applications and users proliferate, so do security risks. Our App and API solution family secures your enterprise with an award-winning WAAP, bot management, API security, and DDoS protection that give you the visibility into threats and the attack defenses you need. Get protections that automatically update, self-tune to your policies, and maintain high performance even while fighting off botnets or record-setting DDoS attacks.
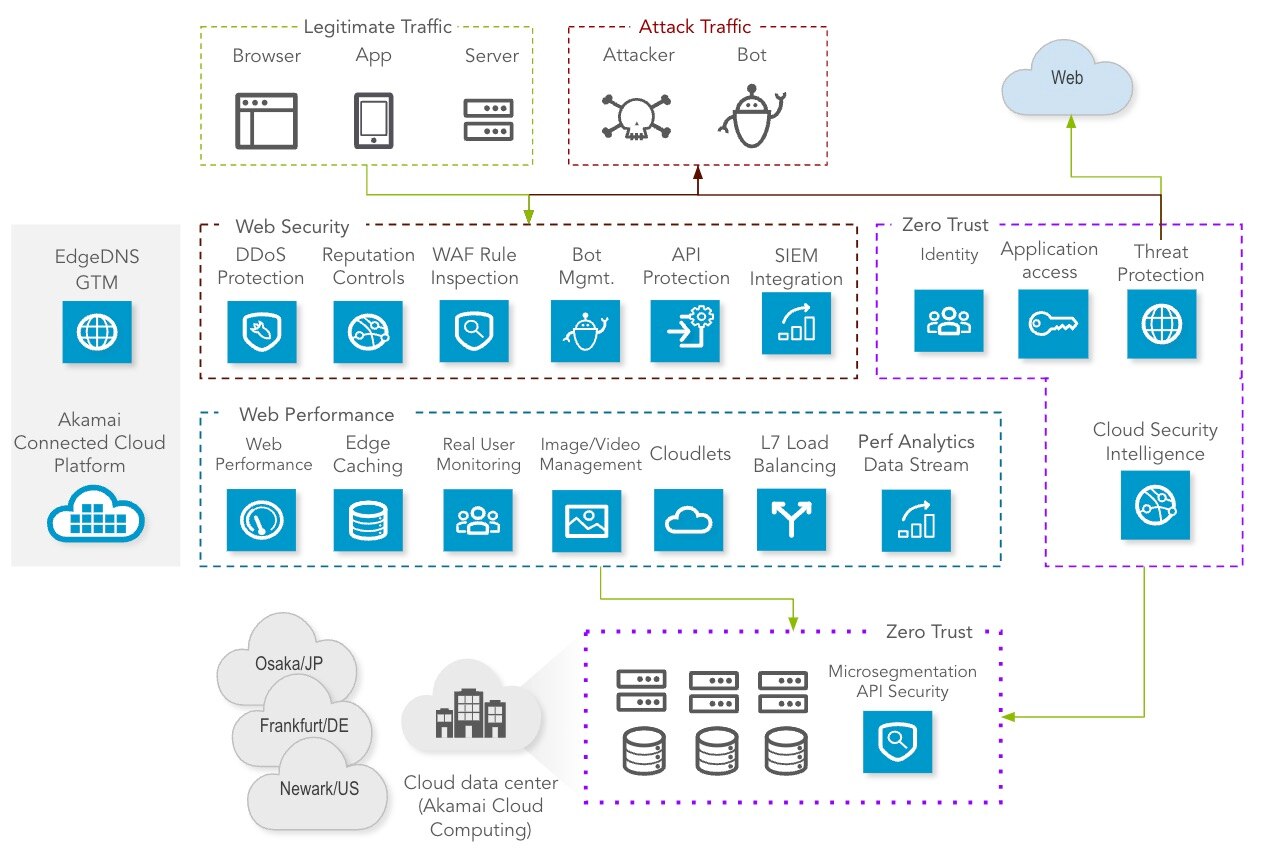
Web Application & API Protection + Advanced API Security
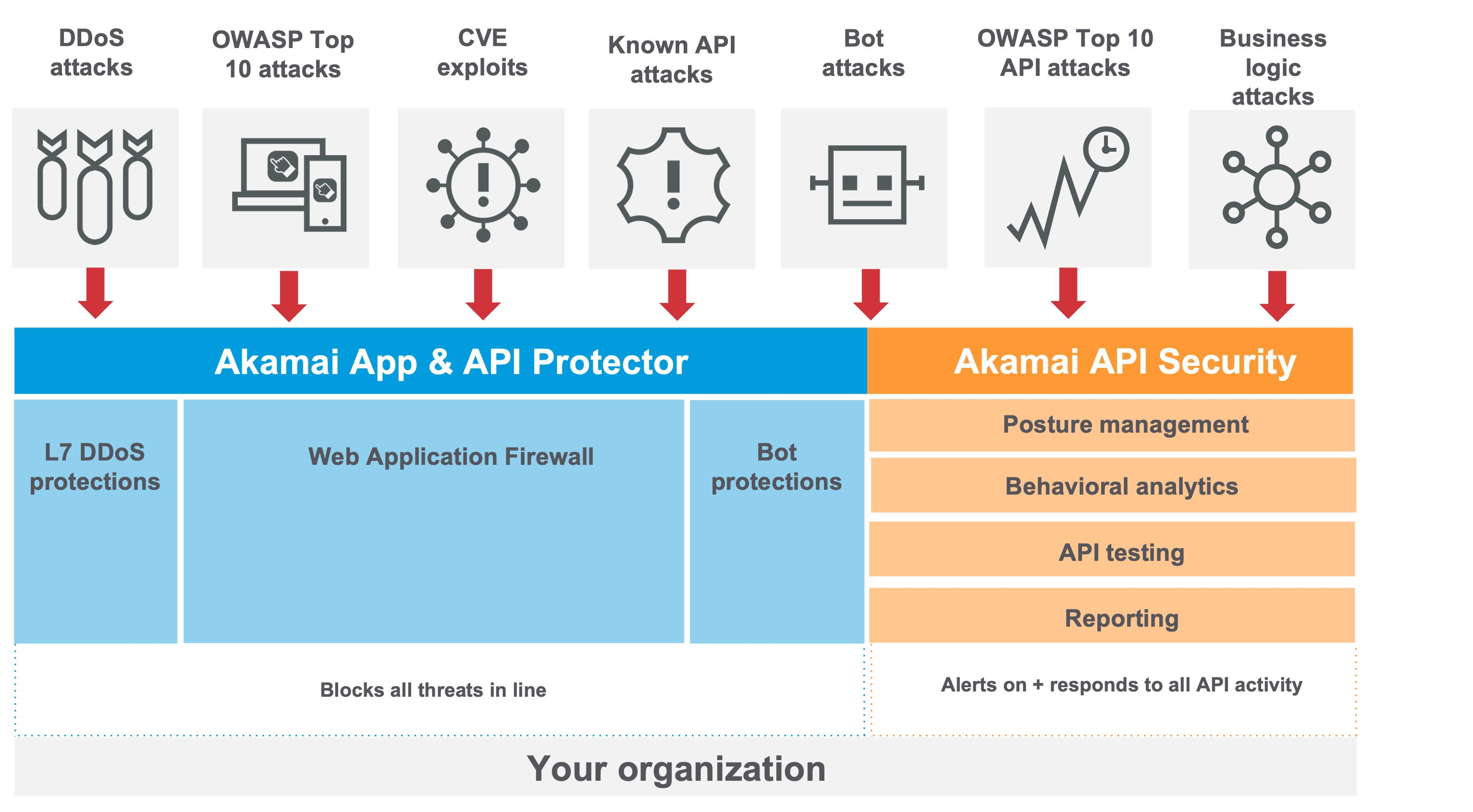
Application and API Protector
App & API Protector is a single solution for web application firewall, bot mitigation, API security, and DDoS, including Layer 7 DDoS protection. Quickly identify vulnerabilities and mitigate threats across the most complicated web and API architectures. The leading attack detection solution on the market, App & API Protector is easy to implement and use, with automatic security updates and holistic visibility into traffic and attacks.
Akamai API Security
API Security gives you full visibility into your entire API estate through continuous discovery and monitoring. It conducts a risk audit of every discovered API, identifies common vulnerabilities, and uses behavioral analytics to detect threats and logic abuse within this fast-growing attack surface.
Edge DNS
Secure and performant DNS. In-cloud, on-prem, or hybrid. Akamai Edge DNS is the most scalable hybrid DNS solution that provides comprehensive security, unmatched performance, and intuitive management. Comprehensive security. DNS attacks are rapidly increasing. Protect your DNS infrastructure from the largest and the most sophisticated attacks in-cloud, on-prem, or as a hybrid. Unmatched performance. Utilize the world’s most distributed network to alleviate origin load, get 24/7 availability, and reduce page load time. Intuitive management. Self-service UI to provision, configure, and manage DNS zones, traffic, policies, and much more!
Global Traffic Management
Everyone connected to your enterprise expects instant gratification and a secure, dynamic experience every time they access your website or application, no matter where they are or what device they’re using. To meet expectations and capture opportunities, IT organizations must aim for zero downtime while ensuring the consistently optimal response times that deliver the best online experiences.
Stop lateral movement with granular controls Protect your organization’s critical assets with Akamai Guardicore Segmentation. It's fast. Uses software-based segmentation to prevent attackers reaching your most sensitive information, versus slower infrastructure segmentation approaches. It's simple. Easy to deploy and manage, giving your IT teams the visibility and control they need to enforce Zero Trust principles across your data centers, multiclouds, and endpoints. It's intuitive. Prevents malicious lateral movement in your network through the application of precise segmentation policies based on visual insights from across your entire environment.
Enterprise Application Access
Akamai Enterprise Application Access is a Zero Trust Network Access solution offering precise access to private applications, based on identity and context. It uses identity-based policies and real-time data such as user location, time, and device security to ensure that users’ only have access to the applications they need and eliminates network level access. It works seamlessly with Akamai MFA for strong user authentication.
Akamai MFA
Eighty percent of reported security breaches involve compromised user credentials or poor password hygiene. These vulnerabilities can result in account takeovers that allow attackers to obtain initial access, then move laterally to discover and exfiltrate data. Adding multi-factor authentication (MFA) as an additional login security layer significantly reduces risk, but many of today’s MFA solutions have significant security flaws. Current second-factor authentication methods can easily be manipulated by attackers and bypassed using simple phishing or social engineering techniques.